SLAU367P October 2012 – April 2020 MSP430FR5041 , MSP430FR5043 , MSP430FR50431 , MSP430FR5847 , MSP430FR58471 , MSP430FR5848 , MSP430FR5849 , MSP430FR5857 , MSP430FR5858 , MSP430FR5859 , MSP430FR5867 , MSP430FR58671 , MSP430FR5868 , MSP430FR5869 , MSP430FR5870 , MSP430FR5872 , MSP430FR58721 , MSP430FR5887 , MSP430FR5888 , MSP430FR5889 , MSP430FR58891 , MSP430FR5922 , MSP430FR59221 , MSP430FR5947 , MSP430FR59471 , MSP430FR5948 , MSP430FR5949 , MSP430FR5957 , MSP430FR5958 , MSP430FR5959 , MSP430FR5962 , MSP430FR5964 , MSP430FR5967 , MSP430FR5968 , MSP430FR5969 , MSP430FR5969-SP , MSP430FR59691 , MSP430FR5970 , MSP430FR5972 , MSP430FR59721 , MSP430FR5986 , MSP430FR5987 , MSP430FR5988 , MSP430FR5989 , MSP430FR5989-EP , MSP430FR59891 , MSP430FR5992 , MSP430FR5994 , MSP430FR59941 , MSP430FR6005 , MSP430FR6007 , MSP430FR6035 , MSP430FR6037 , MSP430FR60371 , MSP430FR6041 , MSP430FR6043 , MSP430FR60431 , MSP430FR6045 , MSP430FR6047 , MSP430FR60471 , MSP430FR6820 , MSP430FR6822 , MSP430FR68221 , MSP430FR6870 , MSP430FR6872 , MSP430FR68721 , MSP430FR6877 , MSP430FR6879 , MSP430FR68791 , MSP430FR6887 , MSP430FR6888 , MSP430FR6889 , MSP430FR68891 , MSP430FR6920 , MSP430FR6922 , MSP430FR69221 , MSP430FR6927 , MSP430FR69271 , MSP430FR6928 , MSP430FR6970 , MSP430FR6972 , MSP430FR69721 , MSP430FR6977 , MSP430FR6979 , MSP430FR69791 , MSP430FR6987 , MSP430FR6988 , MSP430FR6989 , MSP430FR69891
14.2 AES Accelerator Operation
The AES accelerator is configured with user software. The bit AESKLx determines if AES128, AES192, or AES256 is going to be performed. There are four different operation modes available, selectable by the AESOPx bits (see Table 14-1).
Table 14-1 AES Operation Modes Overview
| AESOPx | AESKLx | Operation | Clock Cycles |
|---|---|---|---|
| 00 | 00 | AES128 encryption | 168 |
| 01 | AES192 encryption | 204 | |
| 10 | AES256 encryption | 234 | |
| 01 | 00 | AES128 decryption (with initial roundkey) is performed | 215 |
| 01 | AES192 decryption (with initial roundkey) is performed | 255 | |
| 10 | AES256 decryption (with initial roundkey) is performed | 292 | |
| 10 | 00 | AES128 encryption key schedule is performed | 53 |
| 01 | AES192 encryption key schedule is performed | 57 | |
| 10 | AES256 encryption key schedule is performed | 68 | |
| 11 | 00 | AES128 (with last roundkey) decryption is performed | 168 |
| 01 | AES192 (with last roundkey) decryption is performed | 206 | |
| 10 | AES256 (with last roundkey) decryption is performed | 234 |
The execution time of the different modes of operation is shown in Table 14-1. While the AES module is operating, the AESBUSY bit is 1. As soon as the operation has finished, the AESRDYIFG bit is set.
Internally, the AES algorithm’s operations are performed on a two-dimensional array of bytes called the State. The State consists of four rows of bytes, each containing four bytes, independently if AES128, AES192, or AES256 is performed. The input is assigned to the State array as shown in Figure 14-2, with in[0] being the first data byte written into one of the AES accelerators input registers (AESADIN, AESAXDIN, and AESXIN). The encrypt or decrypt operations are then conducted on the State array, after which its final values can be read from the output with out[0] being the first data byte read from the AES accelerator data output register (AESADOUT).
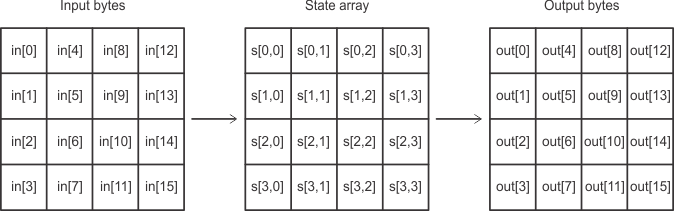 Figure 14-2 AES State Array Input and Output
Figure 14-2 AES State Array Input and Output If an encryption is to be performed, the initial state is called plaintext. If a decryption is to be performed, the initial state is called ciphertext.
The module allows word and byte access to all data registers—AESAKEY, AESADIN, AESAXDIN, AESAXIN, and AESADOUT. Word and byte access cannot be mixed while reading from or writing into one of the registers. However, it is possible to write one of the registers using byte access and another using word access.
NOTE
General Access Restrictions
While the AES accelerator is busy (AESBUSY = 1):
- AESADOUT always reads as zero.
- The AESDOUTCNTx counter, the AESDOUTRD flag, and the AESDINWR flag are reset.
- Any attempt to change AESOPx, AESKLx, AESDINWR, or AESKEYWR is ignored.
- Writing to AESAKEY, AESADIN, AESAXDIN, or AESAXIN aborts the current operation, the complete module is reset (except for the AESRDYIE, AESOPx, and AESKLx), and the AES error flag AESERRFG is set.
AESADIN, AESAXDIN, AESAXIN, and AESAKEY are write-only registers and always read as zero.
Writing data into AESADIN, AESAXDIN, or AESAXIN influences the content of the corresponding output data; for example, writing in[0] alters out[0], writing in[1] alters out[1], and so on. However, interleaved operation is possible; for example, first reading out[0] and then writing in[0], and continuing with reading out[1] and then writing in[1], and so on. This interleaved operation must be either byte or word access on in[x] and out[x].
Access Restriction With Cipher Modes Enabled (AESCMEN = 1)
When cipher modes are enabled (AESCMEN = 1) and a cipher block operation is being processed (AESBLKCNTx > 0), writes to the following bits are ignored, independent of AESBUSY: AESCMEN, AESCMx, AESKLx, AESOPx, and AESBLKCNTx. Writing to AESAKEY aborts the cipher block mode operation if AESBUSY = 1, and the complete module is reset (except for AESRDYIE, AESOPx, and AESKLx).