SLAU367P October 2012 – April 2020 MSP430FR5041 , MSP430FR5043 , MSP430FR50431 , MSP430FR5847 , MSP430FR58471 , MSP430FR5848 , MSP430FR5849 , MSP430FR5857 , MSP430FR5858 , MSP430FR5859 , MSP430FR5867 , MSP430FR58671 , MSP430FR5868 , MSP430FR5869 , MSP430FR5870 , MSP430FR5872 , MSP430FR58721 , MSP430FR5887 , MSP430FR5888 , MSP430FR5889 , MSP430FR58891 , MSP430FR5922 , MSP430FR59221 , MSP430FR5947 , MSP430FR59471 , MSP430FR5948 , MSP430FR5949 , MSP430FR5957 , MSP430FR5958 , MSP430FR5959 , MSP430FR5962 , MSP430FR5964 , MSP430FR5967 , MSP430FR5968 , MSP430FR5969 , MSP430FR5969-SP , MSP430FR59691 , MSP430FR5970 , MSP430FR5972 , MSP430FR59721 , MSP430FR5986 , MSP430FR5987 , MSP430FR5988 , MSP430FR5989 , MSP430FR5989-EP , MSP430FR59891 , MSP430FR5992 , MSP430FR5994 , MSP430FR59941 , MSP430FR6005 , MSP430FR6007 , MSP430FR6035 , MSP430FR6037 , MSP430FR60371 , MSP430FR6041 , MSP430FR6043 , MSP430FR60431 , MSP430FR6045 , MSP430FR6047 , MSP430FR60471 , MSP430FR6820 , MSP430FR6822 , MSP430FR68221 , MSP430FR6870 , MSP430FR6872 , MSP430FR68721 , MSP430FR6877 , MSP430FR6879 , MSP430FR68791 , MSP430FR6887 , MSP430FR6888 , MSP430FR6889 , MSP430FR68891 , MSP430FR6920 , MSP430FR6922 , MSP430FR69221 , MSP430FR6927 , MSP430FR69271 , MSP430FR6928 , MSP430FR6970 , MSP430FR6972 , MSP430FR69721 , MSP430FR6977 , MSP430FR6979 , MSP430FR69791 , MSP430FR6987 , MSP430FR6988 , MSP430FR6989 , MSP430FR69891
14.2.11.2.2 CBC Decryption
For CBC decryption, the first block of data needs some special handling because the output must be XORed with the Initialization Vector. For that purpose, the DMA triggered by 'AES trigger 0' must be configured to read the data from the Initialization Vector first and then must be reconfigured to read from the ciphertext.
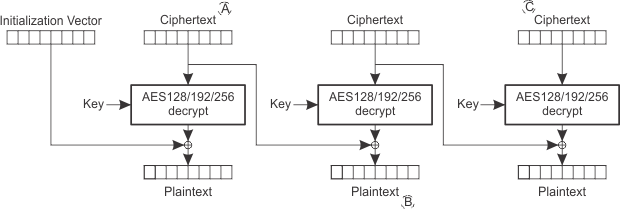 Figure 14-9 CBC Decryption
Figure 14-9 CBC Decryption To implement the CBC decryption without CPU interaction, three DMA channels are needed. Static DMA priorities must be enabled. The DMA triggers must be configured as level-sensitive triggers.
Table 14-6 AES and DMA Configuration for CBC Decryption
| AES
CMEN |
AES
CMx |
AES
OPx |
DMA_A
Triggered by 'AES trigger 0' |
DMA_B
Triggered by 'AES trigger 1' |
DMA_C
Triggered by 'AES trigger 2' |
|---|---|---|---|---|---|
| 1 | 01 | 01 or 11 | Write the previous ciphertext block to AESAXIN | Read plaintext from AESADOUT | Write next plaintext to AESADIN, which also triggers the next decryption |
The following pseudo code snippet shows the implementation of the CBC decryption in software:
CBC_Decryption(key, IV, plaintext, ciphertext, num_blocks)
// Pseudo Code
{
Generate Decrypt Key:
Configure AES:
AESCMEN= 0; AESOPx= 10;
Write key into AESAKEY;
Wait until key generation completed;
Configure AES for block cipher:
AESCMEN= 1; AESCMx= CBC; AESOPx= 11;
AESKEYWR= 1; // Use previously generated key
Setup DMA:
DMA0: Triggered by AES trigger 0,
Source: IV, Destination: AESAXIN,
Size: 8 words, Single Transfer mode
DMA1: Triggered by AES trigger 1,
Source: AESADOUT, Destination: plaintext,
Size: num_blocks*8 words, Single Transfer mode
DMA2: Triggered by AES trigger 2,
Source: ciphertext, Destination: AESADIN,
Size: num_blocks*8 words, Single Transfer mode
Start decryption:
AESBLKCNT= num_blocks;
Wait until first block is decrypted: DMA0IFG=1;
Setup DMA0 for further blocks:
DMA0: // Write previous cipher text into AES module
Triggered by AES trigger 0,
Source: ciphertext, Destination: AESAXIN,
Size: (num_blocks-1)*8 words, Single Transfer mode
End of decryption: DMA1IFG=1
}